Improve Phishing Detection With SLAM
 There are plenty of good reasons why phishing hovers at the top of the list for security awareness training. For the last couple of decades, it has remained the main delivery method for all types of criminal attacks. Ransomware, credential theft, database breaches, and more often launch via a phishing email someone fell for.
There are plenty of good reasons why phishing hovers at the top of the list for security awareness training. For the last couple of decades, it has remained the main delivery method for all types of criminal attacks. Ransomware, credential theft, database breaches, and more often launch via a phishing email someone fell for.
Why has phishing remained a massive threat for so long? Simply because it works. Scammers continually change their methods as technology progresses. These days, they use AI-based tactics to target phishing more efficiently, as just one example.
If phishing didn’t work, scammers would figure out another type of attack. Given that phishing works through human psychology, however, that hasn’t been the case. People continue to fall for it. Because humans are humans, they open malicious file attachments, click on dangerous links, and reveal passwords all the tiem.
As of May 2021, phishing successes increased by 281%. Then in June, they spiked another 284% above May’s numbers.
Studies show that at 6 months after training on cybersecurity, phishing detection skills wane. Employees start forgetting what they’ve learned, and cybersecurity inevitably suffers as a result.
Mnemonics work. Want to give employees a “hook” they can use to remember what they learned? Introduce the SLAM method of phishing identification and avoidance.
What is the SLAM Method for Phishing Identification?
One of the best mnemonic devices known to help people remember information is acronyms. SLAM is an acronym for four priority areas of an email message to check before trusting it or clicking on anything.
These are:
S = Sender
L = Links
A = Attachments
M = Message text
By giving team members the term “SLAM” to use, it’s quicker and easier for them to check emails and suspect the correct ones. This device helps them to avoid missing vital clues. All they need is to use the cues in the acronym.
Check the Sender
Always check the sender of an email thoroughly. Often, cybercriminals will either steal an email address or use a look-alike. Plenty of people mistake a spoofed address for the real thing.
In this phishing email caught out of the wild below, the email address domain is “@emcom.bankofamerica.com.” This wannabe scammer is impersonating the Bank of America. Criminals count on users not paying close enough attention, so this is one way that scammers try to trick you, by putting the real company’s URL inside their fake one.
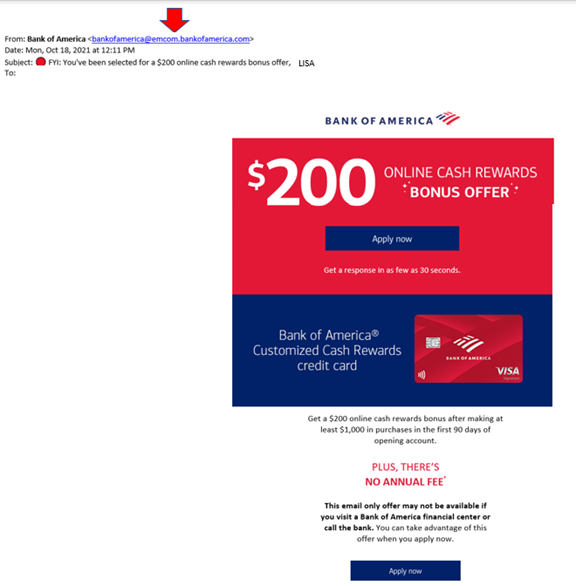
Obviously, the email is very convincing. This one has likely tricked many victims into divulging their personal details. After all, anyone applying for a credit card must provide a Social Security Number, income, birthdate, and more.
Running a quick search on the email address quickly reveals the scam. It’s a trap used in both email and text based phishing attacks.
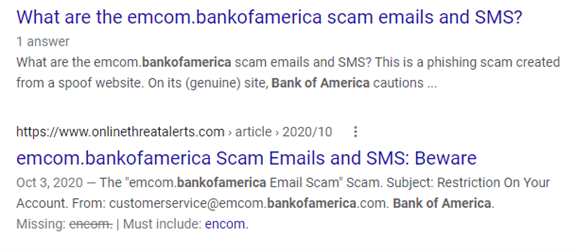
Type an email address into Google and any scam warnings quickly come up, indicating a phishing email.
Hover Over Links Without Clicking
Hyperlinks come over email all the time. They can often get past any installed antivirus/anti-malware filters. After all, those filters are looking for file attachments that contain malware. However, a link to a malicious site doesn’t contain any dangerous code, it’s just a link. Instead, it links to a site that will absolutely swipe everything it can.
Links come in the form of hyperlinked words, images, and buttons in any given email. While on a computer, always hover the mouse cursor over links without clicking on them to reveal the true URL. It’ll usually pop up right next to the cursor. This often can immediately call out a fake email scam.
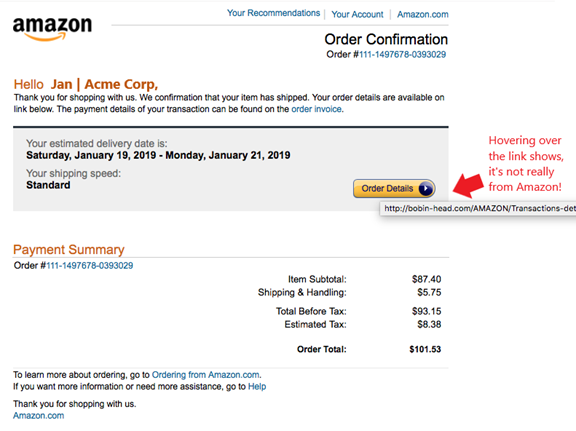
Problems more often occur when looking at email on a mobile device. It’s trickier to see the URL without clicking on it. There is no mouse to hover with as there is on a PC. When using a touch driven device, it’s best not to click or touch the URL at all. Instead, visit the purported site independently to check on the message.
Never Open Unexpected, Unfamiliar or Strange File Attachments
File attachments are unfortunately still widely used as parasites on phishing emails. Messages may show up with them attached, promising a large sale order or invoice. The recipient might see what they think is a familiar word document and open it automatically.
As time goes on, it’s getting harder to know what file formats to avoid. Cybercriminals have become savvier about infecting all types of documents with malware, even those previously thought safe. There have even been PDFs with malware embedded. PDFs used to be the gold standard of not infected, but those days are over.
Never open strange or unexpected file attachments. Always use an antivirus/anti-malware app or program to scan all attachments before opening.
Read the Message Carefully
As a society, we’re great at scanning through text as tech has progressed and information piles up. Scanning like that helps us process loads of incoming information each day in a reasonable time. Unfortunately, scammers are counting on that. When you rush through a phishing email, you miss some telltale signs that it’s a fake.
For example, look again at the phishing example posted above in the “Links” section. You’ll find a small error in grammar within the second sentence. Did you spot it the first time you looked?
The sentence says, “We confirmation that your item has shipped,” instead of “We confirm that your item has shipped.” These little types of errors can be hard to spot, but are always a big red flag that the email is not legitimate. Real business people make sincere efforts to get their spelling and grammar correct.
Why Is This Published By A Business Phone Company?
Here at NoContractVoIP, we believe that your success is our success. To get the latest helpful content delivered to your inbox every month, subscribe to our newsletter here.
Looking for the finest stress-free custom business telephone systems? Contact us or call today at 866-550-0005!
